Key highlights:
- Embargo group laundered $34M via crypto targeting US healthcare and industries.
- Linked to BlackCat hackers; demands reached $1.3M per attack on hospitals.
- Group uses AI-enhanced phishing, exploits poorly regulated exchanges globally.
The Embargo ransomware group cashed out $34 million through cryptocurrency transactions during just nine months of operation, according to analysis by TRM Labs.
Experts traced a complex money-laundering scheme that funneled ransom payments from victims, including hospitals, pharmaceutical firms, and manufacturing plants across the United States, to high-risk exchanges and mixers.
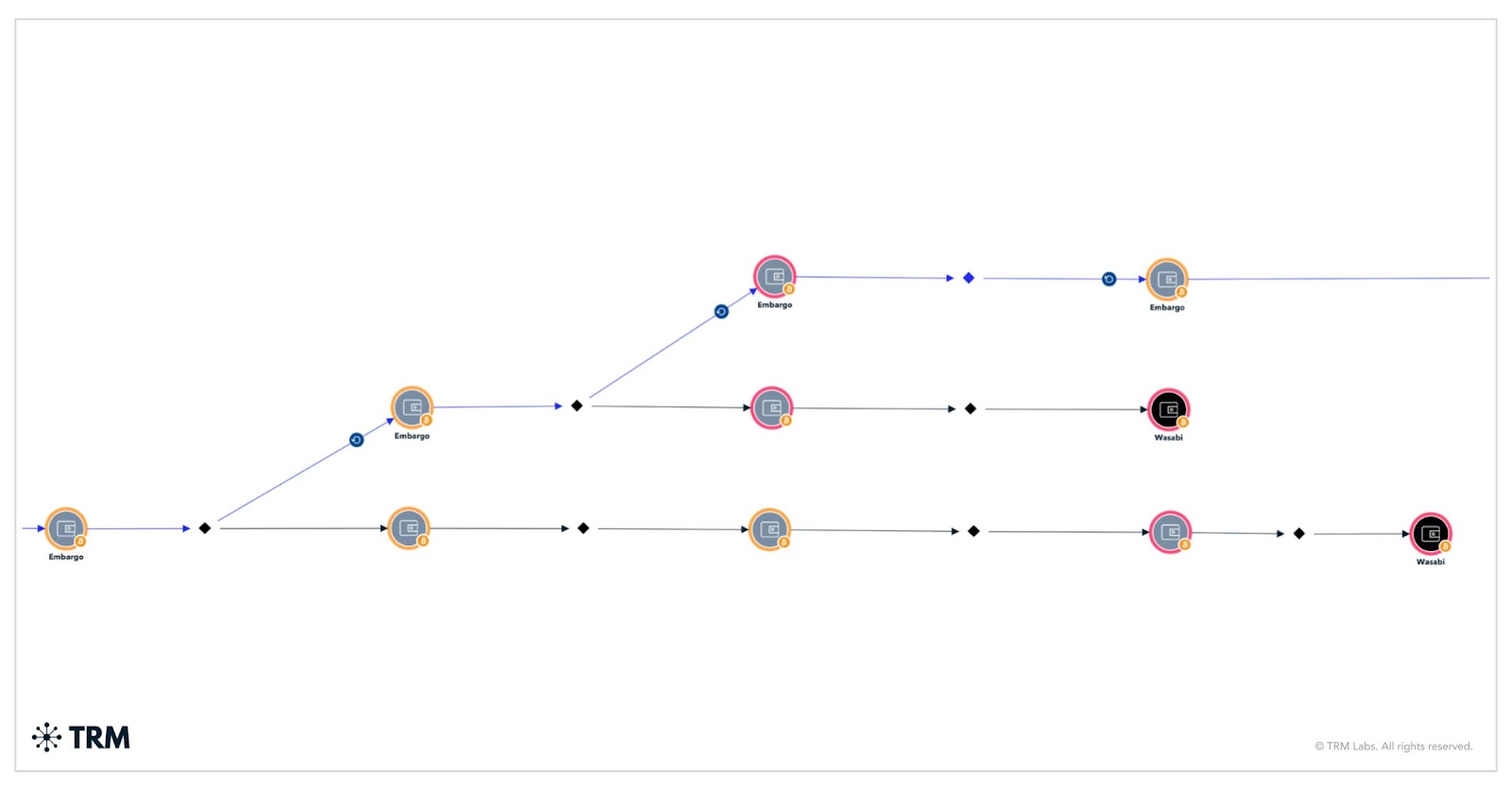
Deposits containing Embargo funds being moved to the Wasabi mixer. Image source: TRMLabs
From BlackCat to Embargo: A rebranded threat
TRM Labs identifies Embargo as the evolved incarnation of the notorious BlackCat/ALPHV group.
This conclusion is based on clear technical overlaps such as the use of the Rust programming language to develop malware, similarity in stolen-data publication websites, and a shared cryptocurrency infrastructure.
It appears the same criminal operators have simply rebranded while continuing their illicit activities.
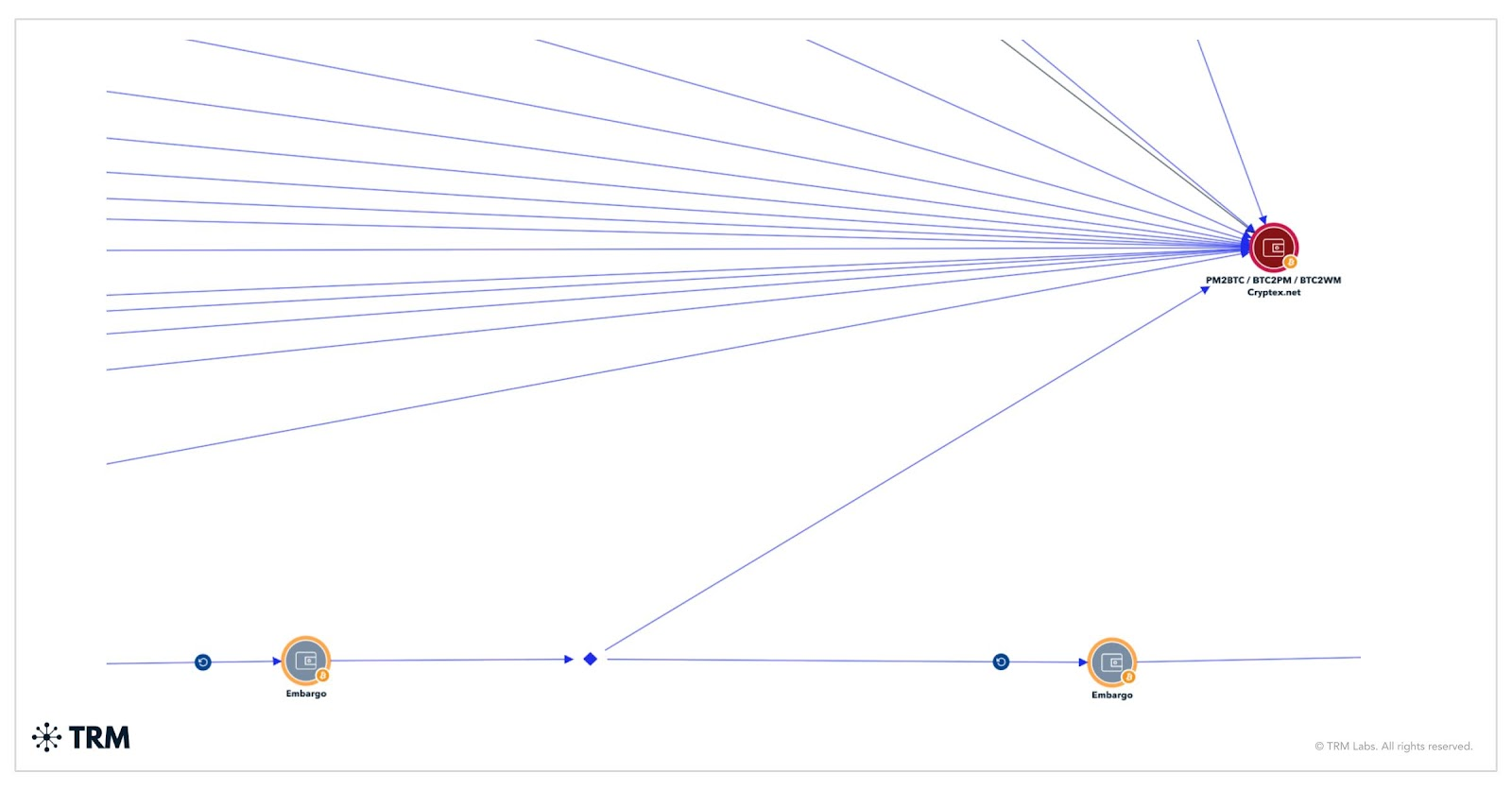
TRM’s Graph Visualizer showing a small Embargo wallet cluster with incoming BlackCat (ALPHV) exposure. Image source: TRMLabs
Victims reportedly include American Associated Pharmacies, Memorial Hospital and Manor in Georgia, and Weiser Memorial Hospital in Idaho. Ransom demands have escalated as high as $1.3 million per attack.
Experts emphasize the particularly cruel nature of assaults on medical institutions, where human lives depend on continuous service.
Tracing the cryptocurrency payment path
The ransomware payments typically move from victim wallets through intermediate addresses before reaching high-risk exchanges, peer-to-peer platforms, and mixing services.
TRM Labs documented hundreds of deposits totaling approximately $13.5 million on global crypto platforms and $1 million through 17 deposits on the now-defunct Cryptnex.net exchange. Contrary to common assumptions, Embargo rarely employs mixers, recording only two deposits to the Wasabi mixer.
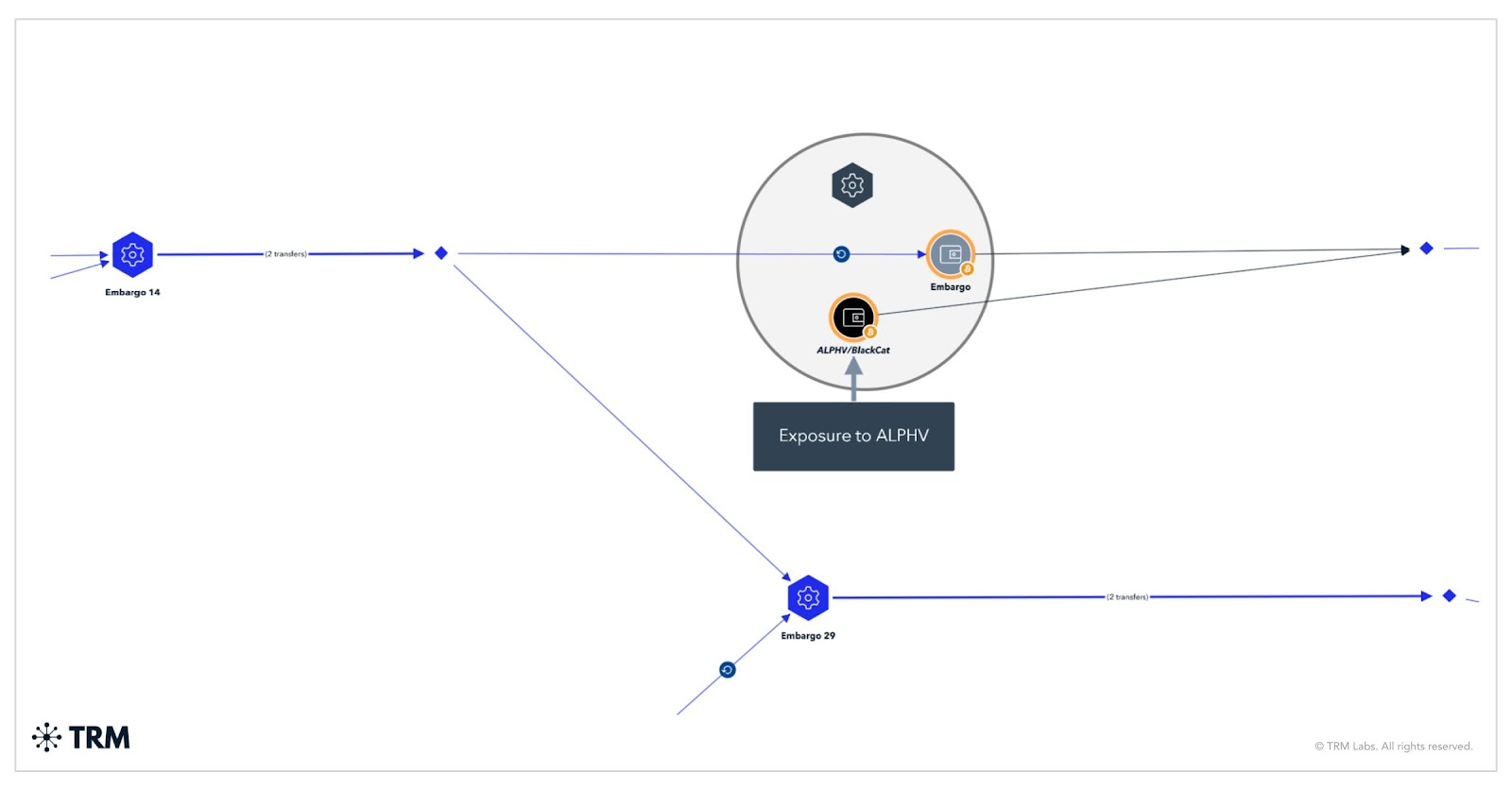
Embargo deposits to Cryptnex.net. Source: TRMLabs
Intriguingly, $18.8 million of the group’s illicit proceeds remain parked at unattributed, dormant addresses, a tactic likely intended to complicate law enforcement tracking or to wait for more opportune conditions for withdrawal.
Innovation and risks in criminal operations
Operating under a ransomware-as-a-service model, Embargo maintains a discreet profile to avoid drawing law enforcement attention while scaling its operations.
Increasingly alarming is the group’s use of artificial intelligence and machine learning techniques to craft sophisticated phishing lures and constantly mutate malware to evade detection and defenses.
Embargo’s ongoing activities highlight vulnerabilities in the cryptocurrency ecosystem, especially related to payments and offshore exchange regulation.
Despite increasing regulatory pressure, loopholes persist, allowing ransomware operators to continue large-scale, profitable campaigns.
Source:: Embargo Hacker Group Laundered $34 Million via Cryptow in Nine Months